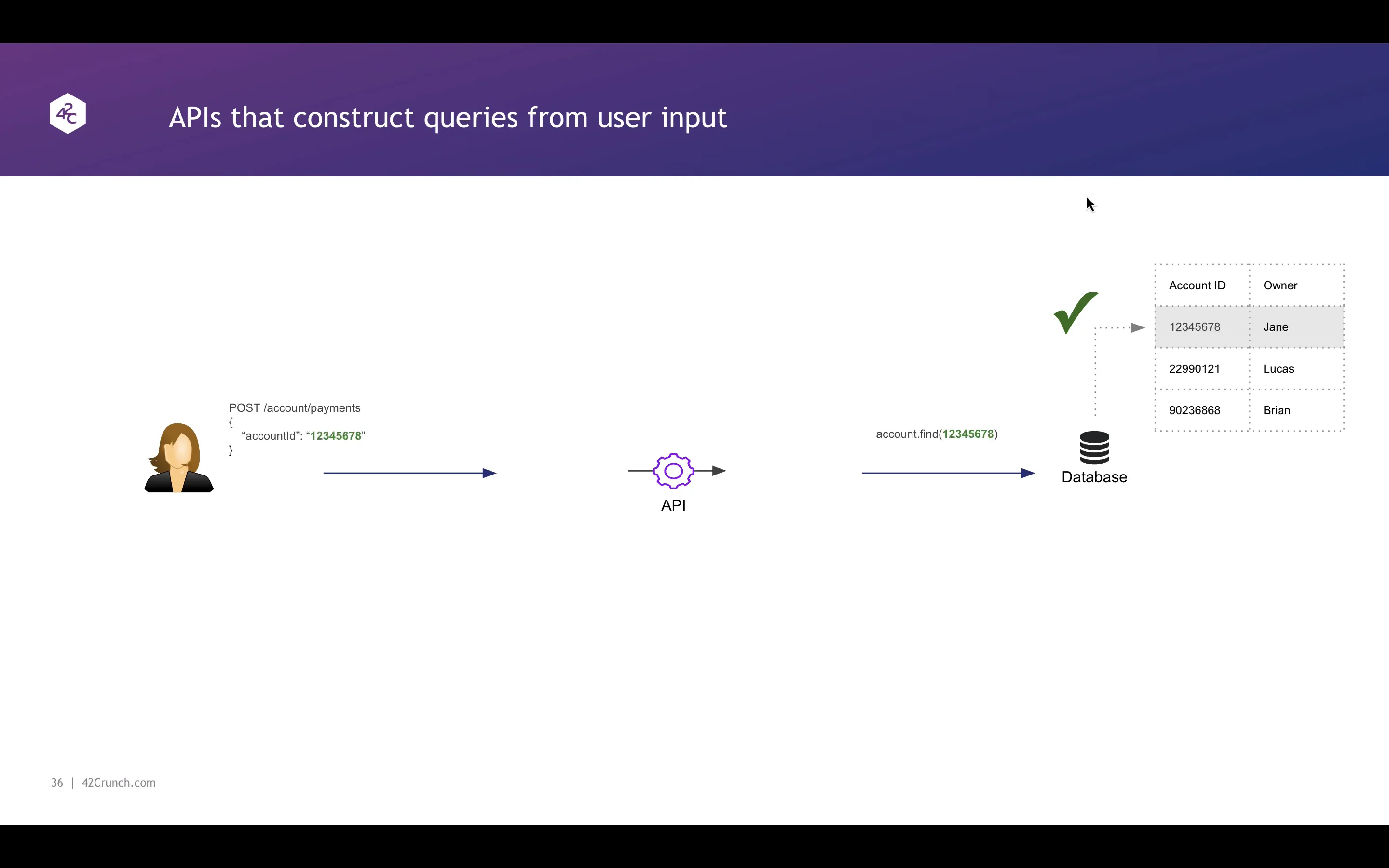
Injection attacks are commonly used by hackers to penetrate a system through an API.
If your API is connected to a downstream component such as a database, a server or network device, or a SaaS or GenAI platform say, then chances are your API code constructs queries, commands or prompts based on input from a user or client.
Learn about secure API development to avoid injection vulnerabilities in your code.